

Traditional network security models are no longer enough to combat advanced and modern cyber threats. The growing number of remote workers, cloud services, and mobile devices has expanded the attack surface, making networks more vulnerable. That’s where Zero Trust Architecture comes in, a modern security framework that is fast becoming the future of network security.
Zero Trust Architecture (ZTA) is a security model that operates on the principle of “never trust, always verify.” Unlike the traditional perimeter-based approach, Zero Trust assumes that threats can exist both outside and inside the network. Therefore, no user or device is trusted by default even if they are inside the corporate network.
Zero Trust Architecture verifies every access request as if it originates from an open network. It requires strict identity verification, device compliance checks, and continuous monitoring before granting access to data or resources. Access is granted based on the principle of least privilege, users only get access to what they absolutely need.
Core components of ZTA include:
By eliminating implicit trust, Zero Trust significantly reduces the chances of data breaches caused by insider threats or compromised devices.
As more businesses shift to remote and hybrid work models, Zero Trust offers secure access from any location, improving flexibility without compromising security.
ZTA helps organizations meet regulatory requirements like GDPR, HIPAA, and PCI DSS by enforcing strong access control and data protection measures.
Zero Trust is ideal for cloud environments, offering scalable protection for SaaS applications, cloud storage, and virtual networks.
Zero Trust Architecture is not just a trend, it’s a necessary evolution in the face of modern cyber threats. As organizations strive to protect their digital assets in an increasingly complex landscape, adopting a Zero Trust approach is essential for future-ready network security. By trusting nothing and verifying everything, businesses can build a resilient, secure infrastructure that stands strong against evolving threats.
For further reading on similar topics, check out article on : How to Conduct a Basic Network Scan for Vulnerabilities
Top 5 Cybersecurity Certifications to Boost Your Career
In this era, cybersecurity professionals are in high demand. Whether you’re starting out or advancing your IT security career, the right certification can open doors to top roles and higher salaries. If you’re looking for the Top 5 Cybersecurity Certifications, here’s a list of must-have credentials offered by TechByHeart Academy to strengthen your skills and boost your profile.
The CEH V13 certification is globally recognized and validates your skills in identifying vulnerabilities and preventing cyberattacks. This program at TechByHeart Academy is designed with live practical sessions, hands-on labs, and real-world hacking scenarios, ensuring you learn to think like a hacker and protect systems effectively.
CHFI focuses on digital forensics. This certification teaches you how to investigate cyber crimes, gather digital evidence, and prepare forensic reports that stand up in court. TechByHeart Academy’s CHFI program is ideal for those aiming to work with law enforcement, incident response, or cyber law.
For those looking to step into or advance in Security Operations Center (SOC) roles, the ASA certification is essential. The course dives deep into threat hunting, incident detection, and advanced SIEM management. With TechByHeart Academy’s state-of-the-art labs, you’ll handle complex attack scenarios, preparing you for high-level SOC analyst roles.
The CSA certification is perfect for freshers and IT professionals who want to specialize in monitoring and responding to cybersecurity incidents. TechByHeart Academy’s CSA course includes real-time security event monitoring and incident analysis, providing a strong foundation for SOC operations.
CST is tailored for those aiming to excel in penetration testing and vulnerability assessments. Through TechByHeart Academy, you’ll perform network and application tests in simulated environments, learn to exploit security flaws, and generate professional reports, critical skills for any ethical hacker or security consultant.
All these certifications from TechByHeart Academy come with hands on labs, expert mentorship, and placement assistance. With their practical-oriented approach, you won’t just pass exams, you’ll build the confidence to tackle real-world cybersecurity challenges.
Earning any of these Top 5 Cybersecurity Certifications can set you apart in a competitive market. Whether you dream of becoming an ethical hacker, forensic investigator, or SOC specialist, TechByHeart Academy has the right course to kickstart or elevate your cybersecurity career.
Ready to secure your future? Enroll now and start your journey toward becoming a sought-after cybersecurity professional!
Is Public Wi-Fi Safe? Here’s What You Should Know

In today’s hyper connected world, public Wi-Fi is everywhere in coffee shops, airports, hotels, and malls. It’s incredibly convenient, especially when you’re on the go and need quick internet access. But while public Wi-Fi might be free, it could come with hidden costs like the risk of your personal data being exposed to cybercriminals.
So, is public Wi-Fi safe? Let’s break it down.
One of the most common threats on public networks is a Man-in-the-Middle (MitM) attack. This occurs when a hacker intercepts the communication between your device and the website or service you’re using. They have the ability to steal financial information, login credentials, and other private information.
Certain public Wi-Fi networks do not use encryption, so the information you send and receive is not secure. Your online activities could be intercepted by anyone on the same network.
Cybercriminals often set up rogue Wi-Fi networks that mimic legitimate ones. If you connect to one of these “evil twin” hotspots, the hacker can monitor everything you do online including logging into email or bank accounts.
Some attackers exploit vulnerabilities in public Wi-Fi networks to inject malware into your device. Once infected, they can monitor your activity, steal data, or lock you out of your own files through ransomware.
Using public Wi-Fi doesn’t have to be risky if you take the right precautions. Here are some smart steps you can take to protect yourself:
A VPN encrypts your internet traffic, making it nearly impossible for hackers to intercept or read your data. It’s the most effective tool for securing your connection on public networks.
Try not to log in to banking sites or enter personal information while on public Wi-Fi. Save those tasks for a secure, private network.
When connected to public Wi-Fi, disable file sharing, Bluetooth, and Airdrop (on iOS) to prevent unauthorized access.
Always check that the websites you visit use HTTPS not just HTTP. The “S” stands for secure and indicates encrypted communication between your web browser and the website.
Outdated apps and operating systems may have vulnerabilities that hackers can exploit. Regular updates help keep your device protected.
Although public Wi-Fi is very helpful, it’s not always secure. In a world that prioritizes digitalization, it is crucial to recognize the risks and take preventative measures to safeguard your data. Make sure you connect safely and use your browser sensibly, whether you’re checking your emails in a coffee shop or making a travel reservation at the airport.
Remember: If it’s free, you might be the product.
For further reading on similar topics, check out article on : How to Protect Your Smartphone from Cybersecurity Threats: A Complete Guide
Troubleshooting Common Installation Errors in Kali Linux on Virtual Machines(A beginner-friendly troubleshooting guide to save you from installation headaches!)
Installing Kali Linux in a virtual machine (VM) like VirtualBox or VMware is a great way to dive into cybersecurity without messing up your main system. But let’s be real—sometimes things go wrong, and error messages can feel like they’re written in alien code. If you’ve ever stared at a frozen installer or a cryptic error, don’t panic! I’ve been there too, and in this guide, I’ll walk you through the most common Kali Linux VM installation fails—and how to fix them.
What’s happening?
* Failed to install linux-image-amd64
* The kernel could not be installed
Why?
How to Fix It:
(Pro Tip: If it keeps failing, try a different Kali ISO version—sometimes the latest one has quirks.)
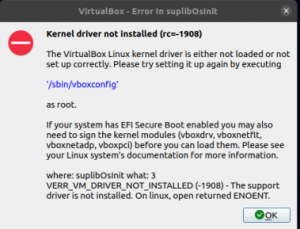
Error Message:
mount: mounting /dev/sda on /media failed: Invalid argument
Why?
How to Fix It:
(If you’re not sure, stick with the automatic installer—it’s way easier!)
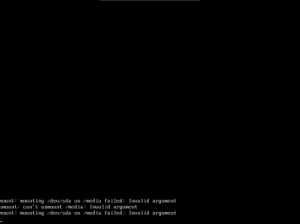
The Problem:
How to Fix It:
✔ In manual partitioning:
✔ If GRUB fails:
(Still stuck? Try reinstalling with “Guided Partitioning” instead of manual.)
What’s happening?
Why?
How to Fix It:
– sudo apt update && sudo apt install kali-linux-default
🔄 Try a different Kali ISO if it keeps failing.
(Fun fact: You can install Kali with just a command line first, then add a GUI later!)
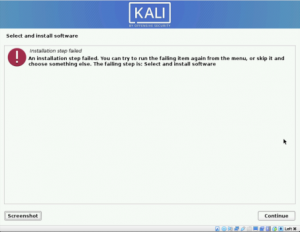
Error Message:
No space left on device
Why?
How to Fix It:
Resize the VM disk (if using VirtualBox):
VBoxManage modifyhd kali.vdi –resize 30000 # Expands to 30GB
Or, just recreate the VM with a bigger disk (easier for beginners).
(Pro Tip: Use dynamically allocated storage so the disk grows as needed.)
🔹 Use the latest Kali ISO (get it from kali.org).
🔹 Enable virtualization (VT-x/AMD-V) in your BIOS for better performance.
🔹 Allocate enough resources:
🔹 Check logs if stuck ( Ctrl + Alt + F4 switches to terminal view).
Kali Linux is an amazing tool, but VM installations can be tricky. If you hit a wall, don’t give up! Most errors are fixable with the right tweaks. Which error did you run into? Let me know in the comments—I’ll help troubleshoot! (And if this guide saved you hours of frustration, share it with another aspiring hacker!)
For further reading on similar topics, check out article on : How to Configure Network Adapters in VirtualBox: A Complete Guide
Top Beginner-Friendly CTF Platforms and Challenges to Start Your Cybersecurity Journey
Ever wanted to “hack” like in the movies—but legally and ethically? Capture The Flag (CTF) challenges are your gateway into the exciting world of cybersecurity. Whether you’re a total newbie or just dipping your toes into hacking, CTFs offer a fun, hands-on way to learn real skills.
In this guide, I’ll break down:
✔ What CTFs are (and why they’re awesome for beginners)
✔ The best beginner-friendly platforms to start with
✔ Easy challenges to try today
✔ Pro tips to avoid frustration & level up faster
Let’s dive in!
Imagine a game where you solve puzzles, crack codes, and find hidden “flags”—but instead of treasure, you’re uncovering cybersecurity secrets! CTFs simulate real-world hacking scenarios in a safe, legal environment, making them perfect for learning.
1. Jeopardy-Style (Best for beginners!)
– challenges in categories like Web Hacking, Cryptography, Forensics.
– You solve tasks to find hidden flags (e.g., FLAG{Th1s_1s_4_Fl4g}).
2. Attack-Defense (Advanced)
– Teams hack each other’s systems while defending their own.
👉 If you’re new, stick with Jeopardy-style CTFs—they’re like mini cybersecurity escape rooms!
– Ever read about SQL injection but had no clue how to actually exploit it?
– CTFs force you to apply theory in real challenges.
– No risk of breaking laws (unlike randomly testing websites).
– All challenges are designed to be hacked.
– CTFs teach you to think like an attacker, spotting weaknesses before bad
guys do.
– Employers love CTF experience—it proves you can solve real problems.
(Fun fact: Many pro hackers started with CTFs!)

Why?
– Walkthroughs & guided learning paths (like “Complete Beginner”).
– No setup needed—hack directly in your browser!
– Free tier available (paid unlocks more content).
Start Here:
– Room: “Intro to Cybersecurity”
– Room: “OverTheWire Bandit” (Linux basics)

Why?
– Beginner-friendly machines with step-by-step tutorials.
– Gradually increases difficulty.
– Free tier + VIP for extra challenges.
Try This:
– “Tier 0 Machines” (Easy boxes with guided help)

Why?
– Teaches Linux commands through a fun, game-like format.
– No installations—just SSH into their server!
– 100% free.
First Challenge:
– Level 0 → 1: Basic SSH login & file navigation.
(Pro tip: If you don’t know Linux yet, start here!)

Why?
– Designed for high schoolers (but great for all beginners).
– Simple, fun challenges with hints & solutions.
– Free & annual competition (with prizes!).
Try:
– “General Skills” challenges (basic commands, encoding).
| Platform | Challenge | What You’ll Learn |
| TryHackMe | “Google Dorking” | How hackers use Google to find secrets |
| HTB | “Meow” (Tier 0) | Basic network scanning & login bypass |
| OverTheWire | Bandit Level 1-5 | Linux commands ( ls , cat , ssh ) |
| PicoCTF | “Obedient Cat” | Reading files & finding flags |
(Just copy-paste the platform name into Google to find them!)
(Don’t worry—you’ll learn these as you go!)
CTFs might seem hard at first, but every expert was once a beginner. The key? Consistency. Solve one challenge a day, and in a few months, you’ll be shocked at how much you’ve learned.
“The only way to learn hacking is to hack (ethically)!”
Which platform will you try first? Let me know in the comments! 👇
(Share this guide if it helped you—more hackers = safer internet!) 🚀💻
Understanding Malware and Its Detection
Let me tell you a story about my friend Sarah. Last month, she clicked on what looked like a harmless PDF attachment in an email. Within hours, her computer slowed to a crawl, strange pop ups appeared, and worst of all – all her family photos were locked behind a ransom demand. That’s malware in action, and it’s scarier than any horror movie because it’s real.
In this guide, I’ll walk you through the dark world of malicious software using plain language and real examples. No tech jargon, just straight talk about how these digital threats work and – more importantly – how you can protect yourself.
Imagine malware as a gang of digital criminals, each with their own specialty:
Remember the “ILOVEYOU” outbreak in 2000? That was a virus that spread through email attachments disguised as love letters. Like a biological virus, it needed someone to open the attachment to spread. Today, viruses still hide in:
Worms are the ninjas of malware. The infamous WannaCry attack in 2017 didn’t need anyone to open a file – it slithered through network connections on its own, encrypting files in hospitals, businesses, and government systems worldwide.
That “free” game crack or “urgent Flash Player update” you downloaded? Could be a Trojan. I once helped a small business owner who installed what he thought was accounting software, only to find his bank accounts emptied days later.
Picture this: You arrive at work and every file has been renamed to “PAY_OR_LOSE_YOUR_DATA.” That’s ransomware. The city of Baltimore was paralyzed for weeks by a ransomware attack that cost over $18 million to recover from.
Some malware doesn’t break things – it watches you. There are cases where spyware has:
Your computer has ways of telling you something’s wrong – you just need to listen:
The “This Doesn’t Feel Right” Signs:
When It’s Really Bad:

After helping dozens of people recover from infections, here’s what actually works:
Free tools like Malwarebytes (for scanning) combined with Windows Defender (always-on protection) catch most threats. For businesses, I recommend paid solutions like Bitdefender GravityZone.
That “update available” notification you keep ignoring? That’s like leaving your front door unlocked. The WannaCry worm only worked because people hadn’t installed a Windows update that patched the vulnerability.
Keep:
Ask yourself:
Cybercriminals are getting craftier:
1. –Tonight: Run a full malware scan and check for pending updates
2. – This Week: Set up automatic backups if you haven’t already
3. – This Month: Have a family meeting about online safety (yes, really)
Remember Sarah from the beginning? After her ordeal, we set up proper backups and security. When another attack came six months later, she simply wiped her computer and restored everything – no panic, no ransom paid. That’s the power of being prepared. Stay safe out there!
For further reading on similar topics, check out article on : What Is Social Engineering? | The Psychology of Social Engineering
Is a Cybersecurity Course Really Worth It in 2025?
In 2025, cybersecurity is no longer optional; it’s essential. As cyber threats become more advanced and frequent, the demand for qualified professionals is exploding. This brings us to a key question many students and working professionals are asking: Is a Cybersecurity Course Really Worth It in 2025?
With companies relying heavily on digital infrastructure, the risks of data breaches, ransomware, and cyberattacks are at an all-time high. From small startups to global corporations, organizations are investing millions in cybersecurity systems and, more importantly, in cybersecurity talent.
Cybersecurity roles are no longer limited to tech companies. Healthcare, finance, education, retail, and even government sectors now require specialists to protect sensitive data. This shift has created a global talent gap, with millions of job openings projected by the end of 2025.
Today’s cybersecurity courses are designed to equip learners with both foundational knowledge and hands-on experience. A good course should include:
– Real-time simulation labs
– Practical ethical hacking sessions
– Industry-recognized certifications
– Access to expert mentors
– Placement assistance
One institution leading this movement in India is TechByHeart Academy.

TechByHeart Academy is one of Kerala’s fastest-growing EC Council-accredited cybersecurity training institutes, offering in-depth, career-focused courses tailored to meet industry demands. The TechByHeart provides:
– Certified Ethical Hacking (CEH) and other globally accepted certifications
– Hands-on labs and real-world projects to build practical skills
– Expert trainers with industry experience
– Placement support and career guidance for students
– A strong presence in Kochi, Kottakkal, Trivandrum, Bengaluru, Chennai, UAE & UK, helping local talents tap into global job markets
Whether you’re a student fresh out of school or a working professional looking to switch careers, TechByHeart Academy offers flexible programs that make cybersecurity education accessible and impactful.
Cybersecurity specialists are among the highest-paid IT professionals in 2025. Job roles such as Security Analyst, Penetration Tester, Cybersecurity Consultant, and SOC Analyst are in high demand. With the right training from institutes like TechByHeart Academy, students can confidently pursue careers not only in India but also in international markets like the UAE, the US, and Europe.
So, is a cybersecurity course really worth it in 2025? If you’re looking to future-proof your career, gain high-income potential, and make a real-world impact, the answer is definitely yes. And with trusted academies like TechByHeart Academy, you can start that journey with the right foundation and support.
How to Set Up Burp Suite for Web Application Testing?Burp Suite is a software tool that is used for Web Application Security Testing. Developed by PortSwigger, it provides a broad set of tools for identifying and exploiting vulnerabilities in web applications. It’s widely used by security professionals, penetration testers, and developers to ensure the security of their applications. In this article, we will learn how to set up Burp Suite.
Burp Suite comes in different editions:
It is a type of proxy server, which means it sits between the user’s web browser and the web server. It’s a versatile tool that includes features like a proxy server for intercepting HTTP/S traffic, Repeater, intruder, scanner, decoder, and more.
1. Proxy: Acts as an intermediary between your browser and the target web application, allowing you to intercept, inspect, and modify HTTP/S traffic. This is essential for understanding how the application communicates and identifying vulnerabilities.
2. Scanner: An automated tool that scans web applications for common security issues like SQL injection, cross-site scripting (XSS), and more. It helps save time by identifying vulnerabilities efficiently.
3. Intruder: A powerful tool for automating customized attacks. It can be used for tasks like brute-forcing login credentials or testing for parameter-based vulnerabilities.
4. Repeater: Allows you to manually modify and resend individual HTTP requests. This is useful for testing specific inputs and observing how the application responds.
5. Sequencer: Analyzes the randomness of tokens, such as session IDs, to determine their predictability. This helps in assessing the security of authentication mechanisms.
6. Decoder: A utility for encoding and decoding data in various formats (e.g., Base64, URL encoding). It’s handy for understanding and manipulating encoded data.
7. Comparer: Compares two pieces of data to highlight differences. This is useful for analyzing changes in responses or identifying subtle variations in application behavior.
8. Reporting: Generates detailed reports that summarize findings and provide actionable insights. This is particularly useful for communicating results to stakeholders.
1. Go to Burp Suite official website and download the installer Link.
2. Select Burp Suite Community Edition and also select your device version.
3. After installing that give the full execution permission using “chmod +x and filename”.
4. And then run the Burp file “./filename.sh”.
5. Complete the setup Wizard , choose the path and complete the setup and click finish.
6. Now go to the path where the Burp Suite is located, and run the BurpSuiteCommunity.
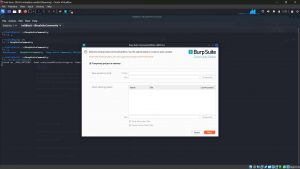
7. Click “Next” and then click “Start Burp”
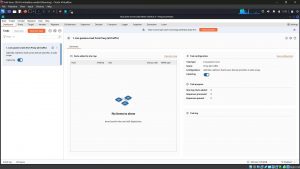
This is how the Burp Suite is Installed , and the next step is to configure the proxy settings.
1. For intercepting the traffic in Burp , you need to configure the proxy settings.
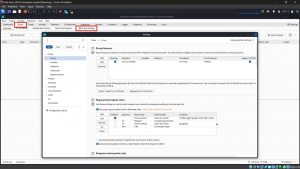
2. You should see an entry in the table with a ticked Checkbox in the Running column, and “127.0.0.1:8080” showing in the Interface column.
3. Go to the proxy section and Turn on Intercept if it is off .
1. Install Foxy Proxy extension in Firefox and set up Proxy settings
2. And configure the Burp Proxy into the foxy proxy
3. In Foxy Proxy , go to the proxy section and , click on add and add a new proxy settings
4. Add a name , Hostname (127.0.0.1) , and port (8080)
5. Go to burp/ or 127.0.0.1:8080 in Firefox.
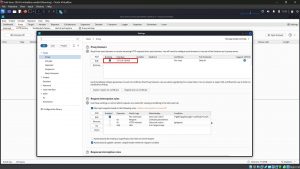
6. The CA cert must be installed in your browser as a trusted root so that the browser will trust the SSL connections made to Burp Suite.
7. Download the CA Certificate and save it.
8. Go to the settings of Firefox and search for “certificates”
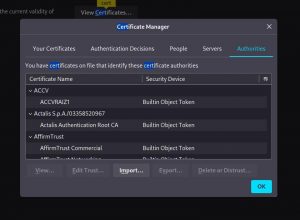
9. Click “Import” and then add the Certificate file that downloaded earlier. Once the Burp’s CA cert is installed you should have no problem using Burp Suite as an interceptor. At Firefox, try to browse anything and you will not see any security warning. At Burp Suite, when the interceptor is turned on, you will see all the requests made by the browser. You can analyze the requests and make any modifications. When you’re satisfied, click on the Forward button to send the message.
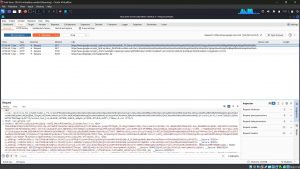
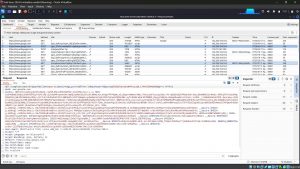
In this blog, you learned how to Set Up Burp Suite in Kali Linux.
Can Cybersecurity Be Replaced by AI? Here’s What Experts SayWritten by Prithul Raj M R
Prithul Raj, a cybersecurity practitioner diving deep into the world of ethical hacking, forensics, and Linux-based security.

In an age where cyber threats evolve at an unprecedented pace, Artificial Intelligence (AI) has emerged as a powerful ally in the battle for digital security. From detecting threats to automating responses, AI plays a growing role in defending networks and data. But one critical question continues to spark debate in the tech world: Can cybersecurity be replaced by AI?
AI has transformed the cybersecurity landscape in several impactful ways:
Threat Detection: AI-powered systems can analyze vast amounts of data in real time to identify suspicious behavior, malware signatures, and potential breaches.
Automation: Repetitive tasks such as scanning for vulnerabilities, applying patches, and isolating infected systems can now be handled faster and more efficiently with AI.
Predictive Analytics: Machine learning models help forecast potential threats before they occur, allowing organizations to adopt proactive strategies.
These capabilities highlight the strengths of AI in supporting cybersecurity operations. However, they don’t provide a complete solution.

Despite its capabilities, AI has limitations:
False Positives: AI can generate alerts for harmless activities, overwhelming security teams, and creating unnecessary panic.
Lack of Contextual Understanding: AI lacks human intuition and judgment. It can struggle to understand the context or motive behind an action, especially in complex social engineering attacks.
Dependency on Quality Data: AI systems are only as good as the data they are trained on. Incomplete or biased datasets can lead to blind spots.
Vulnerability to Attacks: Ironically, AI systems themselves can be targeted by cybercriminals using adversarial inputs or data poisoning.
So, can cybersecurity be replaced by AI? Not entirely, at least not yet.
Cybersecurity is not just about responding to technical threats. It involves strategic thinking, ethical decision-making, and understanding human behavior, areas where humans still excel over machines. Ethical hackers, incident response teams, and security analysts provide critical insights that machines alone cannot replicate.
Furthermore, cybersecurity decisions often carry legal and ethical consequences. Determining the best course of action in a breach scenario isn’t something an AI should handle alone.

Rather than asking can cybersecurity be replaced by AI, a more productive question might be: how can AI enhance human cybersecurity efforts? The future of digital defense lies in a collaborative model where:
AI handles data-heavy and repetitive tasks, improving speed and accuracy.
Humans oversee, analyze, and make strategic decisions, ensuring ethical and contextual accuracy.
This partnership enables faster responses to threats, reduces human error, and allows cybersecurity professionals to focus on higher-level concerns.
So, can cybersecurity be replaced by AI? The answer is no, at least not completely. While Artificial Intelligence (AI) is revolutionizing the way we detect and respond to cyber threats, it is not a substitute for human expertise, intuition, and ethical reasoning. Instead, the future of cybersecurity will depend on how effectively we combine the power of AI with human intelligence.
As threats grow more sophisticated, embracing this hybrid approach will be the key to building a resilient and secure digital world.
How an Ethical Hacking Course Can Transform Your Career in CybersecurityIn today’s hyperconnected world, cybersecurity has evolved from a niche IT concern to a critical business priority. As organizations scramble to protect their digital assets from increasingly sophisticated threats, a new breed of security professional has emerged: the ethical hacker. Taking an Ethical Hacking Course could be the career-defining decision that propels you from the sidelines to the frontlines of this dynamic field.

Unlike malicious hackers who exploit vulnerabilities for personal gain, ethical hackers often called “white hats” use their skills to strengthen security systems. They think like attackers but work for the defenders. An Ethical Hacking Course equips you with this unique perspective, teaching you to identify and address vulnerabilities before they can be exploited. This proactive approach has become invaluable as organizations shift from reactive to preventative security strategies.
What makes these courses so transformative is their comprehensive, hands-on approach. A quality Ethical Hacking Course typically covers:
– Network security fundamentals and vulnerability assessment
– Penetration testing methodologies and exploitation techniques
– Web application security and common attack vectors
– Social engineering tactics and countermeasures
– Cryptography principles and implementation
– Legal and ethical boundaries of security testing
Unlike theoretical training, these courses immerse you in practical scenarios through labs and simulated environments. You’ll experience the thrill of identifying vulnerabilities, executing controlled exploits, and developing mitigation strategies all within a legal, ethical framework.
The career impact of ethical hacking training is immediate and substantial. Graduates often qualify for specialized roles such as:
– Penetration Tester/Ethical Hacker
– Security Analyst/Consultant
– Vulnerability Assessor
– Security Operations Center (SOC) Analyst
– Information Security Manager
Industry-recognized certifications like CEH (Certified Ethical Hacker) or OSCP (Offensive Security Certified Professional), often obtained through an Ethical Hacking Course, serve as powerful credentials that signal your expertise to employers. In a field facing a severe talent shortage, these qualifications can significantly boost your earning potential and job security.
Perhaps the most valuable takeaway from ethical hacking training isn’t a specific technical skill but the development of the “hacker mindset” a unique way of viewing systems and identifying their weaknesses. This perspective transforms how you approach security challenges, enabling you to anticipate threats rather than merely respond to them.
This mindset extends beyond technical scenarios, enhancing your problem-solving abilities and critical thinking skills across all aspects of cybersecurity work. You’ll find yourself noticing vulnerabilities and potential improvements in everyday systems.
In a world where data breaches make headlines daily, ethical hackers stand as the essential line of defense. By investing in your skills today, you position yourself at the forefront of this crucial field, making your career not just financially rewarding but profoundly impactful.